Guest blog by RPost
Guest blogs are written by contributors outside of HawkSoft. The author's views are entirely their own and may not reflect the views of HawkSoft.
The active threat of ransomware is certainly felt in the insurance industry and has been a looming issue for many independent agencies. However, a different type of cyber attack often overlooked by businesses is now causing far greater financial losses: Business Email Compromise (BEC).
The FBI reports that in 2022, $2.7 billion was mis-wired to cybercriminal accounts due to BEC attacks, mostly in small amounts of $10K to $250K; most of it unretrievable. According to the FBI, this form of cybercrime is more lucrative than all others for these organized cybercriminal gangs. In comparison, this amount dwarves the $35 million that was paid in ransomware payments, a mere 1.3% of the losses due to BEC attacks. This article will outline what BEC attacks are, how you can spot the warning signs, and ways you can protect your insurance business from these attacks.
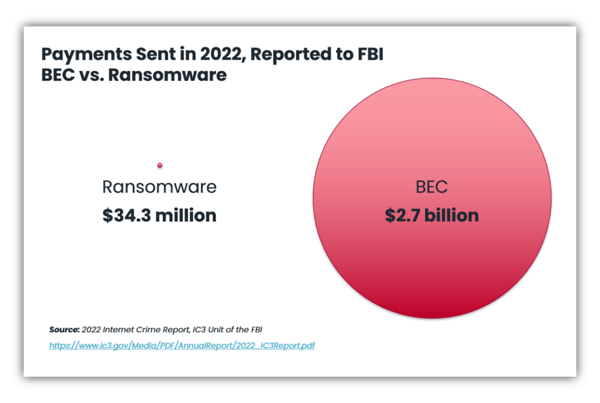
Image credit: RPost
In this article:
- What is a business email compromise (BEC) attack?
- Anatomy of a BEC attack
- How to prevent BEC attacks
- Employee education and training
- Implement Multi-factor Authentication (MFA)
- Email filtering and anti-spam measures
- Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM)
- Specialized email security
What is a business email Compromise (BEC) attack?
For those who are new to this term or how it’s different from ransomware, here is a quick rundown.
Ransomware is a malicious software that encrypts files and systems, demanding a ransom payment for their release. It infects computers through various means and holds data hostage until the ransom is paid.
Business Email Compromise (BEC) refers to a type of cyberattack where imposters exploit email communication to deceive individuals within an organization, typically with the goal of accessing financial or sensitive data. This can include requesting wire transfers, redirecting payments, or disclosing sensitive data. BEC attacks are sophisticated, with imposters sometimes spending weeks or months gathering information about the target organization. These criminals will impersonate yourself and your team members and will build a strong network of contacts, including potentially your own clients and customers.
While you may feel secure in your ability to detect and avert BEC attacks, it's essential to remember that these cybercriminals may not directly target your defenses. Instead, they could aim at the more vulnerable point of your operations – your recipient’s inbox. Their deceptive tactics can lead your team into inadvertently sending funds to an impostor. Thus, vigilance at every point in your communication chain is paramount to guard against these sophisticated threats.
Anatomy of a BEC attack
Here is a play-by-play of what a BEC might look like and how it can catch you off guard:
- You (or your Accounts Receivable team) send an ordinary email to a client or customer about a payment due. Emails like these are sent by the team on a very regular and frequent basis.
- Your recipient’s email account is being unknowingly eavesdropped on by a cybercriminal using a discovered reused password and IMAP protocol at their server, which lets them bypass web login security and mirror the email inbox in another location.
- Within hours of your payment-related email going to your recipient, the cybercriminal copies the email content (often including PDF payment details for a wire or ACH) and changes only one thing—the account where the money is to be sent. All they need is Photoshop and a dream.
Note: These cybercriminals often have legitimate bank accounts at the same major banks that many of us use. So if you usually have payments going to your Bank of America account, for example, they will use that same bank and routing number, but use their own account number. - A second email will arrive in your recipient’s inbox from what appears to be your email address (or a lookalike address, such as your name with a newly purchased domain one letter off from your legitimate domain). To most people it would appear as if you simply sent the email twice, and the recipient usually opens the newer/top-of-the-inbox one, which is from the cybercriminal.
- Seeing an expected invoice with nothing overtly suspicious, your recipient sends the payment to the cybercriminal’s bank account (thinking it was your account) and replies to the imposter email with confirmation.
- The cybercriminal immediately moves the funds from their legitimate bank account to an offshore account. The money is now untraceable and likely gone forever.
How to Prevent BEC Attacks
It may seem like a daunting task to prevent your agency from becoming a victim of such an attack, but you can start with these important tips to protect not only yourself and staff, but also your customers, from becoming another statistic.
1. Employee education and training
Provide your team with comprehensive training on BEC attacks, including common techniques such as the one outlined above, red flags such as receiving double emails, and preventive measures. Teach employees about email security best practices, such as verifying email senders, avoiding clicking on suspicious links or attachments, and using strong passwords. It seems straightforward, but knowing what to look for is half the battle, and taking the time to pause and verify before performing an action will certainly put the odds in your favor.
Technology can also help remind staff to take precautions at the right moment. Email training tools that educate the sender during their normal workflow can be a fantastic addition to automate the attack prevention process.
2. Implement multi-factor authentication (MFA)
Require employees to enable MFA for accessing their email accounts, which adds an extra layer of security by requiring an additional verification step. MFA can help prevent unauthorized email access even if an attacker manages to obtain login credentials through phishing or other means. The more roadblocks you put in place for criminals, the harder it will be for them to find an entry point to launch a convincing BEC attack.
3. Email filtering and anti-spam measures
Utilize robust email filtering systems that can identify and block suspicious emails, phishing attempts, and spoofed email addresses. Implementing anti-spam solutions will minimize the chances of employees receiving malicious or fraudulent emails, and reduce the workload of verifying that every email they receive is legitimate.
4. Sender policy framework (SPF) and domain keys identified mail (DKIM)
SPF and DKIM provide further mechanisms to validate the source of emails, making it harder for attackers to impersonate legitimate senders. Having your IT administrator set up SPF and DKIM records for your organization's email domains will help prevent email spoofing and verify the authenticity of incoming emails. Additionally, you can consider implementing look-alike domain detectors, which can catch out any potential imposter domains.
5. Specialized email security
Specialized email security tools tailored to your unique business case are crucial for detecting and preventing sophisticated business email compromises and cyberattacks that exploit email. Customized solutions provide proactive defense mechanisms, leveraging advanced algorithms and AI to identify anomalies and malicious content. This allows you to easily monitor your agency’s email health and identify specific threats or weak points.
As a solution partner for HawkSoft customers, RPost has specialized in the specific business needs of independent insurance agencies regarding email and e-sign security and compliance for over 20 years. By staying abreast of rising threats such as BEC attacks, independent agencies can implement preventative measures and heighten their security to ensure they keep their business and clients safe.
Handle email Security & Compliance with RMail by RPostRMail provides email privacy and compliance, data leak and human error prevention, and more. For more information on RPost’s products and services or for a free trial, contact partners@rpost.com. |