Independent insurance agencies are no strangers to the topic of data security. With data breaches becoming more and more commonplace, cyber insurance has become the fastest growing segment for US P&C insurers. Your agency might be managing cyber risk for your clients, but are you taking steps to reduce data security risks at your own agency?
While there’s no way to guarantee your agency will never be susceptible to an attack on your systems or data, there are steps you can take to understand and increase the security of your client data. Agencies often think it’s the sole responsibility of the technology systems they use to protect their agency data, but in reality the highest level of data security requires measures from all parties to protect data in every environment it touches.
This article illuminates how data is commonly secured by the systems agencies use, what steps HawkSoft takes to secure data, and areas where agencies can take steps to increase the security of their data.
In this article:
How do technology providers secure client data?
One of the best things an agency can do to protect their client data is to store it in an insurance agency management system that’s built to keep data secure. Management systems and other technology providers typically encrypt client data to keep it secure, and many systems have additional data security measures or certifications. Here’s a little more detail on what that means.
Data encryption
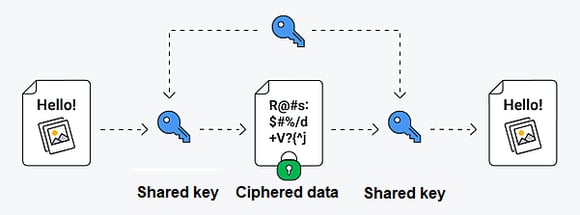
Encryption is the process of encoding data using an algorithm to make it unreadable to outside parties. This protects data on computer and cloud systems by preventing unauthorized entities from making use of the data without the correct encryption/decryption key. You can find a good explanation of data encryption here, but think of it like writing a message to your friend using a code, which your friend has to know in order to read the message. Data is typically encrypted at two times: when at rest (while stored within a system), and when in transit (while being transmitted between two systems).
The data encryption process
When & how does HawkSoft encrypt data?
HawkSoft encrypts data at rest on HawkSoft Version 4.4 and later. This means your client files are automatically encrypted, as well as any attachments you upload. Any client files or attachments that might have been added to HawkSoft before Version 4.4 are automatically encrypted upon opening, or you can identify and batch encrypt all legacy attachments with our Image Encryption tool (search "Image Encryption" in the HawkSoft Help Portal for details).
You may have noticed you can’t edit attachments in HawkSoft – this is because attachments are encrypted when added to the client file, which prevents them from being edited. But if you need the ability to edit an attachment, don’t worry – you can create a working document, which allows multiple users to edit a document on a client file while still keeping the document encrypted and secure. Search "Working Document" in the HawkSoft Help Portal for details on creating and using working documents.
HawkSoft also encrypts data in transit, such as when it is transmitted to and from online hosting partners, HawkSoft Cloud, or API partners. This is done using HTTPS and TLS (transport layer security), which is an additional layer of encryption that provides end-to-end security for data in transit. You may not realize it, but TLS is usually what protects sensitive information you enter on websites, like logins or credit card information.
We also vet the data security of HawkSoft API partners on several levels, including verifying where data accessed from HawkSoft is stored and ensuring partners do not sell data without the permission of the customer.
Will data encryption be different in HawkSoft 6?
In HawkSoft today, client data and attachments are stored on the network as individually encrypted files. In HawkSoft 6, client data and attachments will be stored in databases and blob storage (a flexible solution for storing vast quantities of data of different types in the cloud), both of which are encrypted at the database level, rather than the file level. In short, the level of security will be the same, but the format for encryption will be different. Data in transit will continue to be transmitted through HTTPS using TLS.
Data security certifications
You might want to check whether your agency management system holds any other data security certifications or standards to provide further security for your systems or data. You can see HawkSoft’s cybersecurity statement of compliance for more technical information about data security at HawkSoft.
HawkSoft also employs additional measures to ensure the highest possible security for data, such as conducting penetration testing (simulating a cyber-attack on a computer system to evaluate its security) using an independent third party.
SOC 2 compliance
HawkSoft also operates to the standards of SOC 2 compliance, which certifies that an organization that handles or stores customer data maintains strict standards for the security of all data and systems. HawkSoft has already obtained its Type 1 security certification (audited at a single point in time) and is now in the process of being audited for Type 2 certification (audited again over a 12-month period). In short, we already operate according to SOC 2 standards, and through our continued adherence will receive the second level of certification.
HIPAA compliance
Agencies also sometimes ask us if HawkSoft is compliant with HIPAA (the Health Insurance Portability and Accountability Act), which sets standards for the protection of certain health information. Healthcare organizations like hospitals and doctor’s offices are required to be HIPAA compliant. As HIPAA applies only to healthcare, this is not generally a concern for P&C agencies.
Unfortunately, similar to email encryption, HIPAA compliance requires not only one party to be compliant, but all parties that touch the data. Due to the stringent requirements of HIPAA and our inability to enforce them upon other parties that handle HawkSoft data, such as hosting partners, carriers, or API partners, it’s not feasible for HawkSoft (or most other platforms in the independent insurance industry) to be eligible for HIPAA compliance at this time.
Data masking & user permissions
Many technology platforms also offer security features that mask sensitive data, or PII (personally identifiable information) while it’s onscreen. This hides sensitive information such as social security numbers or date of birth, so that the information won’t be seen by others who may be looking at your screen. HawkSoft masks PII by default on the Personal and Driver screens in the client file. See our article on PII masking in the Help Portal for more information.
In addition, platforms typically allow agency admins to control which users have access to certain data, reports, or areas of the system. For example, HawkSoft allows agency admins to control access to different areas in HawkSoft with user permissions.
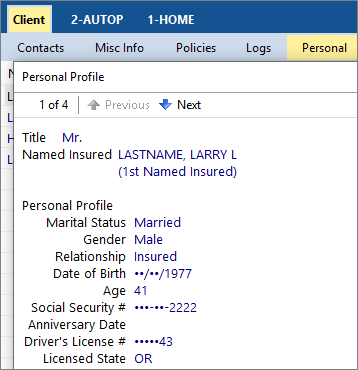 An example of masked PII in HawkSoft
An example of masked PII in HawkSoft
How can agencies further secure their client data?
The agency management system isn’t the only place client data might live or be shared, so agencies share some responsibility in protecting their internal systems, as well as access to those systems. Email, password, and login security are incredibly important areas for agencies to focus on to ensure data remains protected and only accessed by the appropriate parties, as well as creating and storing backups of data.
Ensure email security
One place where sensitive information may be vulnerable is when being sent by email. Because independent agencies communicate so frequently with clients and carriers and may share sensitive data like policy information, this can be a major area of risk.
So what level of security do email providers offer? Unfortunately, while some provide a level of encryption for email, both the sender and the receiver of the email must implement the same level of encryption for it to truly be secure. For example, Gmail employs email encryption, but only when the party they are sending to also employs encryption (see details here). Due to the large number of email providers available, this has not yet been widely standardized or required. As Google points out, “encrypting 100% of all email on the internet requires the cooperation of all online mail providers.”
However, there are still options out there for secure email. Email encryption services or add-ons, such as RMail by Rpost (free) or Microsoft Office 365 E3 (monthly subscription) can provide the best possible security for email. See a list of top email encryption platforms here.
When you send an email from within your management system, remember that it may be using your own email provider to send the message (this is the case with HawkSoft), in which case the security of the email depends on your chosen provider.
Implement password & login security measures
Aside from the systems you use to store client data, another important element of security is regulating access to those systems to prevent malicious parties from gaining access through stolen passwords or other methods. Two of the best ways to achieve this are through password security measures and multi-factor authentication (MFA).
Password security
Implementing strong password security is one of the best things your agency can do to keep your systems and data secure. That includes implementing requirements for strong passwords, using password managers, and following best practices for password security. Read our password security blog for tips on each of these areas.
Multi-factor authentication (MFA)
Modern password security is moving toward requiring multi-factor authentication (MFA) on login, which requires users to verify themselves using a second method—usually a code sent via email or text. This is one of the best ways to prevent unauthorized parties from logging into a system using a stolen password.
The insurance industry is no exception, with bodies like Gramm-Leach-Bliley, NY DFS, and the NAIC Model Security Law requiring businesses to implement MFA to further protect data. ACT’s recent study on MFA found that 60% of carriers said they are implementing MFA for agent portals, comparative raters, and more, with the remaining portion planning to implement MFA in the future.
Take a look at our blog on MFA to learn more about why MFA is important, what types are available, and how to implement it for your agency.
Perform regular backups of agency data
Another crucial piece of the data security puzzle is ensuring you always have access to your agency’s data, even if there is a cyber attack or emergency affecting your agency’s physical workstations. For this reason, it’s best practice to ensure there are regular backups of your agency data performed by either your agency management system provider or your agency. This creates a necessary layer of data redundancy to ensure you have a copy of your data even if your management system, or the workstations that access it, become compromised.
Check out our blog article on data backups for more information on backup options and best practices.
Mitigating risk together
We hope this article helps paint a better picture of what both technology providers and agencies can do to ensure the highest level of protection for client data. We realize that it requires an investment of time, money, and effort for agencies to implement steps such as using secure email, regulating passwords and logins, and creating and storing backups. But we also know independent agencies intimately understand the principles of risk management, which are certainly at play in the arena of data security—small, consistent investments in these areas now will yield tremendous value in the case of a security incident, which could be devastating to your agency. Technology providers and agencies can each take steps to mitigate security risks on their end of the client data cycle.
More on client data: read our data ownership white paperLearn what your agency can do to advocate for ownership of the client data housed in the technology systems you use, and get 3 questions to ask before signing an agreement with a vendor. |